
A pseudorandom number generator may have good statistical properties but be insecure. But a physical RNG with good statistical properties is probably secure.

A pseudorandom number generator may have good statistical properties but be insecure. But a physical RNG with good statistical properties is probably secure.
By Christos Kasparis, EnSilica EETimes (May 15, 2024) The rise of quanum computing paints a significant challenge for the cryptography we rely on today. The modern encryption standards we currently use to safeguard sensitive data and communications, such as DSA, public key RSA and those based on elliptic curves, will eventually be broken by
The impact of quantum algorithms on different cryptographic techniques and what can be done about it.

Current encryption methods will likely be broken by 2030. Embedded systems in development now will have a reasonable chance of encountering attacks.

This article is co-authored by @gracieabot_ Is it a revolution or merely hype? In a world where...

The primes used for Diffie-Hellman key exchange must be chosen carefully to avoid security flaws. This post looks at recommended primes.

In the realm of blockchain technology and cryptocurrencies, the concept of consensus plays a pivotal...

Earlier this week a letter from an activist imprisoned in France was posted to the internet. Contained within Ivan Alococo’s dispatch from the Villepinte prison

Arthur Hayes rubbed success in the Feds’ face and got busted. Now he’s returning to a shell-shocked industry.
The crypto money-laundering market is tighter than at any time in the past decade, and the few big players are moving a “shocking” amount of currency.
Programming errors on the blockchain can mean $100 million lost in the blink of an eye. Ronghui Gu and his company CertiK are trying to help.

The next-generation media outlet navigating the intersection of culture and technology.

Let's say you want to send an encrypted message to your friend in order to avoid it being intercepted...

NIST has formally retired the widely used 27-year-old SHA-1 cryptographic algorithm, bringing cryptographic security into the modern age.

When quantum computers become powerful enough, they could theoretically crack the encryption algorithms that keep us safe. The race is on to find new ones.

Zero-knowledge proofs allow researchers to prove their knowledge without divulging the knowledge itself.
I'm sick of complex blogging solutions, so markdown files in a git repo it is - francisrstokes/githublog

While the core philosophy of blockchains is trustlessness, trusted execution environments can be integral to proof-of-stake blockchains.

As cryptocurrencies have plunged, attention has focused on a potential point of vulnerability: the market’s reliance on a so-called stablecoin called Tether.

I'm not an expert in cryptography — I'm just a developer, and most developers are in this same boat...

When a cryptocurrency’s value is theoretical, what happens if people quit believing?
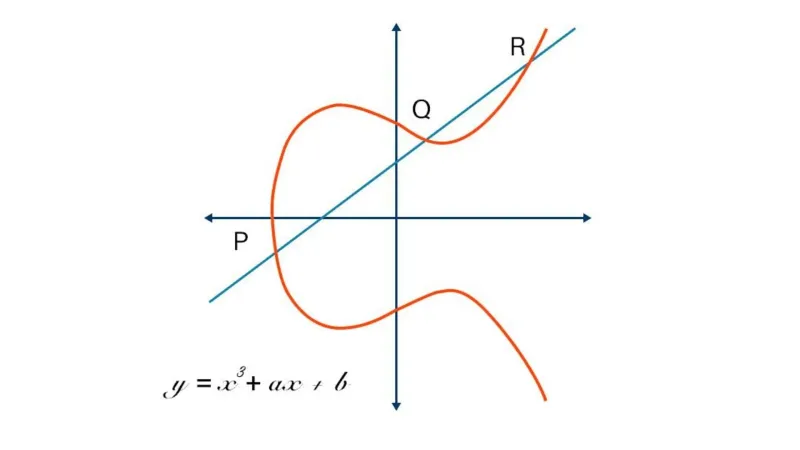
Elliptic Curve Cryptography (ECC) is a modern public-key encryption technique famous for being smaller, faster, and more efficient than incumbents.

Welcome to Video’s customers thought their payments were untraceable. They couldn’t have been more wrong. The untold story of the case that shredded the myth of Bitcoin’s anonymity.

Here at Trail of Bits we review a lot of code. From major open source projects to exciting new proprietary software, we’ve seen it all. But one common denominator in all of these systems is that fo…

Code to help you pull NFT data directly from the source, transform it in a way that’s more familiar, and analyze important NFT data.

The company is undertaking a far-reaching effort to change how it works. For some, it is an echo of their early idealism and a vision for what the internet could have been.

Learn all of the most important blockchain and cryptocurrency terms and jargon here. We add new words and descriptions every week.

A couple allegedly used a “laundry list” of technical measures to cover their tracks. They didn’t work.

Now he’s pulling the strings, and raking in hundreds of millions, from a blockchain rage called DeFi, which promotes the fantasy of democratized financial services.

Cryptocurrency is not merely a bad investment or speculative bubble. It’s worse than that: it’s a full-on fraud.

The Basics Ethereum is a network of computers which collectively form the Ethereum Virtual...

OpenSea is the world's first and largest web3 marketplace for NFTs and crypto collectibles. Browse, create, buy, sell, and auction NFTs using OpenSea today.
Despite considering myself a cryptographer, I have not found myself particularly drawn to “crypto.” I don’t think I’ve ever actually said the words “get off my lawn,” but I’m much more likely to click on Pepperidge Farm Remembers flavored memes about how “crypto” used to mean “cryptography” than ...

Quantum Lab: Scientists are fabricating quantum photonic circuits—consisting of waveguides and other elements—to manipulate single photons for future quantum communications and processing.Oak Ridge National Laboratory / Flickr Nautilus Members enjoy an ad-free experience. Log in or Join now . Justin Trudeau, the Canadian prime minister, certainly raised the profile of quantum computing a few notches […]

Cybersecurity experts tracing money paid by American businesses to Russian ransomware gangs found it led to one of Moscow’s most prestigious addresses.

"NFTs" have hit the mainstream news with the sale of an NFT based digital artwork for $69 million. I thought I'd write up an explainer. Spec...

For those who are just wading into the crypto territory, here’s a basic explainer on how the computer science behind these systems work.

The long read: Last year, three cryptocurrency enthusiasts bought a cruise ship. They named it the Satoshi, and dreamed of starting a floating libertarian utopia. It didn’t work out

A trip through the intentionally unseeable World of Hiding Data in Imagery

A new study shows that quantum technology will catch up with today’s encryption standards much sooner than expected. That should worry anybody who needs to store data securely for 25 years or so.

In 2016 North Korean hackers planned a $1bn raid on Bangladesh's national bank and came within an inch of success. But how did they do it?
How did Ruja Ignatova make $4bn selling her fake cryptocurrency to the world - and where did she go?

Whitfield Diffie and Martin Hellman are researchers who invented a safe method to communicate a password. Their 1976 paper opens with the…

In October 2020, Miami-based art collector Pablo Rodriguez-Fraile spent almost $67,000 on a 10-second video artwork that he could have watched for free online. Last week, he sold it for $6.6 million.
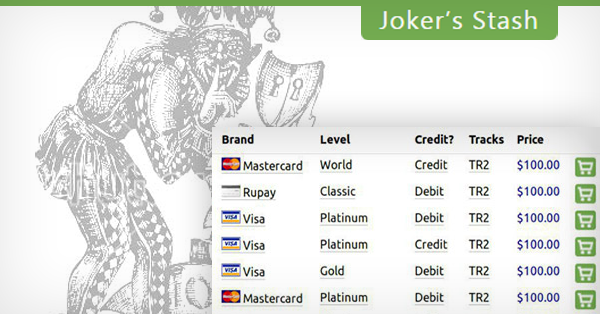
According to Elliptic’s analysis, the founder of one of the most popular carding marketplaces, Joker’s Stash, has retired having amassed a fortune of over $1 billion.

Quantum computers could make encryption a thing of the past, but 15 contenders are trying to prove they have what it takes to safeguard your data.

The distributed ledger technology that started with bitcoin is rapidly becoming a crowdsourced system for all types of verification. Could it replace notary publics, manual vote recounts, and the way banks manage transactions?

After decades of conflict in North Kosovo, all it’s taken for Serb and Albanian politicians to put aside their resentments is the get-rich-quick prospect of cryptomining.

Intro If you're into Cryptography For Beginners, you're in the right place. Maybe you're j...
the official Rust and C implementations of the BLAKE3 cryptographic hash function - BLAKE3-team/BLAKE3

An international team claims its perfect secrecy cryptography is made unbreakable by physics

The race is on to create new ways to protect data and communications from the threat posed by super-powerful quantum computers.

Former U.S. Army Green Beret and a16z crypto deal partner, Alex Pruden served in Iraq, Afghanistan, Kuwait, and Turkey. During this time, he saw first-hand that underlying the Syrian refugee crisis, the rise of radical extremism, and other global conflicts was a lack of trusted institutions. As a result, in times of crisis, the basics... Read More

In 25 concise steps, you will learn the basics of blockchain technology. No mathematical formulas, program code, or computer science jargon are used. No previous knowledge in computer science, mathematics, programming, or cryptography is required. Terminology is explained through pictures, analogies, and metaphors. This book bridges the gap that exists between purely technical books about… Read More »Book: Blockchain Basics: A Non-Technical Introduction in 25 Steps
LitePaper transforms the complex world of crypto, bitcoin and web3 into beautiful bundles of learning.
A simple, accessible recommendation for key sizes and recommended algorithms for various cryptographic algorithms.

How to use polynomials to share secrets, and how to verify that the secret has been shared without unlocking it.

Certificates and public key infrastructure (PKI) are hard. No shit, right? I know a lot of smart people who''ve avoided this particular rabbit hole. Eventually, I was forced to learn this stuff because of what it enables: PKI lets you define a system cryptographically. It''s universal and vendor-neutral yet poorly documented. This is the missing manual.

Let's Encrypt does not currently generate Elliptic Curve certificates. Here's how to obtain one.
Here’s a list of crypto readings and resources (2018-2019). It’s organized from building blocks and basics; foundations (& history); and key concepts — followed by specific topics such as governance; privacy and security; scaling; consensus and governance; cryptoeconomics, cryptoassets, and investing; fundraising and token distribution; decentralized exchanges; stablecoins; and cryptoeconomic primitives and crypto goods (non-fungible... Read More

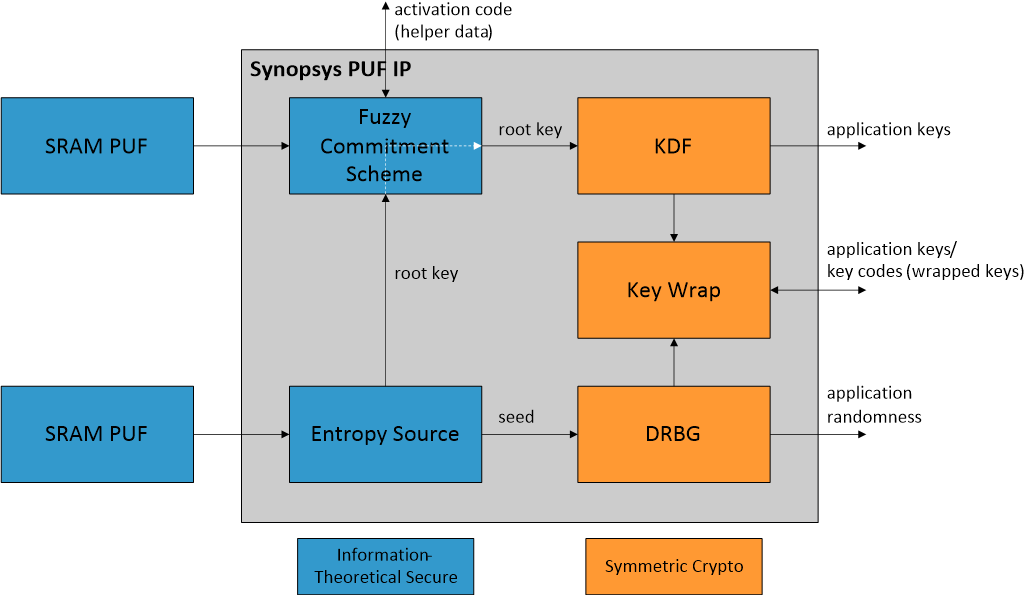
Imperfect Silicon, Near-Perfect Security Physically unclonable functions (PUF) seem tailor-made for IoT security.

Hello all and welcome to Part 3 of building the JackBlockChain — JBC. Quick past intro, in Part 1 I coded and went over the top level math and requirements for a single node to mine its own b…

Cryptographers have researched zero-knowledge proofs for two decades, but the technique is only just now poised to redefine the concept of online privacy.

Last night I figured out what might kill crypto. And it’s not a black swan event. History suggests it’s the natural end of the path we’re on today.