
53.5% of websites have weak SSL setups—leaving attack surfaces exposed and increasing breach risk.

53.5% of websites have weak SSL setups—leaving attack surfaces exposed and increasing breach risk.

These top browser automation tools can automate your repetitive & tedious tasks on the web, including form filling, data scraping, website testing & more. Try them out in 2023 to skyrocket your productivity.

Learn how to get started building a robust continuous deployment pipeline in GitLab. Follow these step-by-step instructions, practical examples, and best practices.

Learn how to modernize continuous integration/continuous deployment, including automating the development, delivery, and security of pipelines.

Containers were a revolutionary jump ahead of virtual machines, and they continue to get faster, lighter and more secure in the years since.

Transitioning the codebase from using environment variables to Rails Credentials for Zero-Downtime Deploys.

A look at what you can do with this tool as well as some of its limitations in comparison to its rivals.
What is a honeypot?A honeypot detects and records attacks when an attacker tries to break into a system. The honeypot we will discuss here is an SSH honeypot. Environment12OS: Ubuntu 24.04 LTS x86_6

We would like to thank Voltage Park, Dell, H5, and NVIDIA for their invaluable partnership and help with setting up our cluster. A special…

Documentation for the npm registry, website, and command-line interface

This post is meant to guide you through some of the lessons I’ve learned while working with multi-terabyte datasets. The lessons shared are focused on what someone may face as the size of the…

You don't get seamless deployments entirely without cost, but some techniques bring lots of benefits with little additional complexity.

UniSuper, a $135 billion pension account, details its cloud compute nightmare.
This is my personal site, where I write about Ruby, programming, and any of my varied fascinations.

Learn from GitLab's 2017 incident: 300GB of data lost in seconds, but their transparent recovery is a masterclass in accountability.

This article describes how to set up Nginx server blocks on Ubuntu 22.04. You'll learn how to set up multiple websites on a single server and customize each site's settings to suit your needs.

We reduced our AWS bill so that we could invest in more important areas.
Assortment of technology startup infrastructure recommendations

Kubernetes is the 800-pound gorilla of container orchestration. It powers some of the biggest deployments worldwide, but it comes with a price tag...
Get your Docker Cheat Sheet as PDF or PNG. In this article, you learn how to write Dockerfiles, build images, and run them as container.
Site Reliability Engineering, incident management, learning, lessons learned, SRE
A collection of documents, slides, and videos about Linux performance, mostly created by Brendan Gregg, and with a focus on performance analysis.
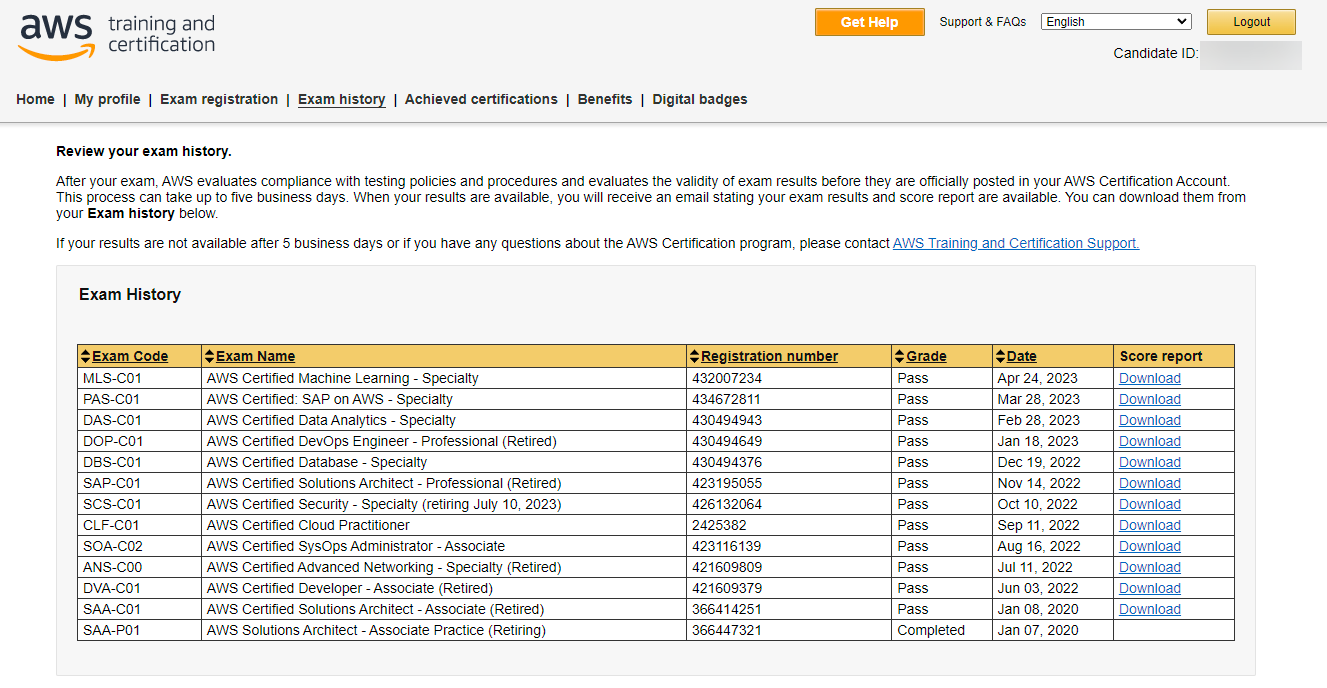
On April 24, 2023, I finished the AWS certification marathon of passing one AWS certification exam per month (“the certification marathon”). This blog post outlines the lessons learned from this journey and expands on the previously published successful blog post On AWS Certifications. Lesson #01 – Certification marathon is a journey While having all AWS...

DORA is a long running research program that seeks to understand the capabilities that drive software delivery and operations performance. DORA helps teams apply those capabilities, leading to better organizational performance.

Scaling becomes a necessary part for your system when your system grows in popularity. There are two...
A collection of inspiring lists, manuals, cheatsheets, blogs, hacks, one-liners, cli/web tools and more. - trimstray/the-book-of-secret-knowledge

#Introduction Have you ever desired you could develop a web application locally on your computer...

Introduction: The software development process has been transformed by the DevOps...

🔐 Introduction to Ansible 🔗Related content You can find repo...

This is an open-source introduction to Bash scripting ebook that will help you learn the basics of Bash scripting and start writing awesome Bash scripts that will help you automate your daily SysOps, DevOps, and Dev tasks...

In this article, we're going to discuss how to use Curl to interact with RESTful APIs. Curl is a command-line utility for transferring data from or to a remote server.

This article was initially published on Lago's blog, an open-source billing API, and was ranked #1 on...
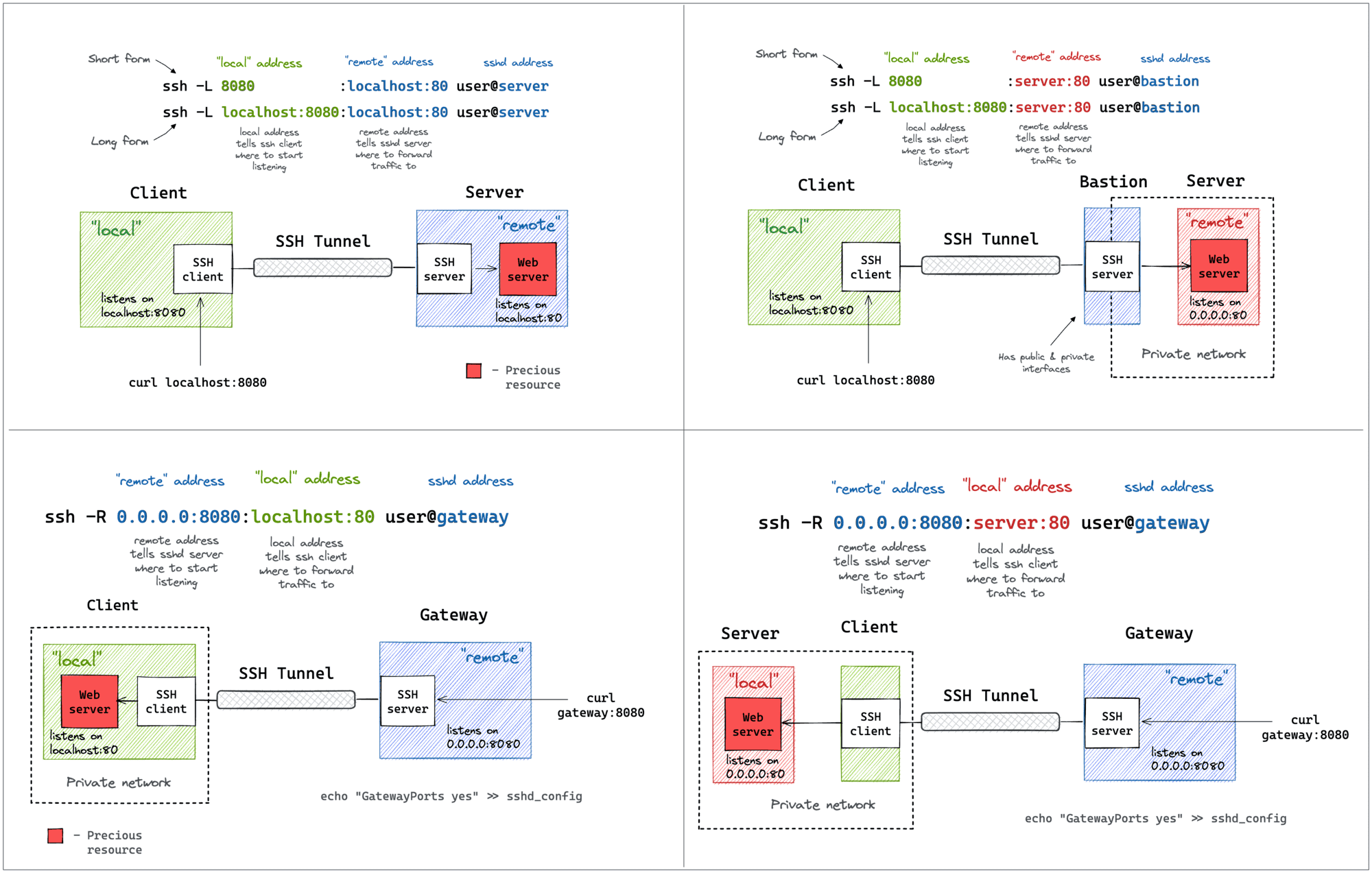
SSH port forwarding explained in a clean and visual way. How to use local and remote port forwarding. What sshd settings may need to be adjusted. How to memorize the right flags.

Capistrano is a deployment automation tool built on Ruby, Rake, and SSH. It allows you to deploy your...

The creation of resources in the cloud and the management of the lifecycle of these resources can be...

GitOps is a methodology for deploying and managing software applications using Git. It is also...

A database is a collection of information that is structured for easy access. It mainly runs in a...

Do you know how many open-source tools are in DevOps? Have you ever seen the picture below? Have...

Photo by Carl Heyerdahl on Unsplash Productivity in software development has always been tricky to...

2013-era server offers rare peek under the hood of Netflix’s Open Connect network.
Linux Troubleshooting Interview DevOps SRE

Steampipe is an open source tool to instantly query your cloud services (e.g. AWS, Azure, GCP and more) with SQL. No DB required.
This all-new update to our popular resource includes tools to evaluate page speed, security, accessibility, regulatory compliance, code, and more.

Heroku will stop offering its free tiers this November, leaving developers to choose other...
The Cyber Swiss Army Knife - a web app for encryption, encoding, compression and data analysis - gchq/CyberChef

Heroku was such a simple and free experience to host side project and start developing. What is the...

Heroku was such a simple and free experience to host side project and start developing. What is the...

Given the recent news about Heroku bringing an end to free dynos and PostgreSQL databases, what other...

We decided early on to store all chat history forever so users can come back at any time and have their data available. This is a lot of data: how do we do it?
ngrok is the fastest way to put anything on the internet with a single command.

You must adopt proper infrastructure automation if you want to enable your teams to achieve faster...
Router Security Home Page
There is a huge and ever-widening gap between the devices we use to make the web and the devices most people use to consume it. It’s also no secret

Hot, strenuous and unsung. There is nothing soft and fluffy about the caretaking work that enables our digital lives

The final goal of all industrial machine learning (ML) projects is to develop ML products and rapidly bring them into production. However, it is highly challenging to automate and operationalize...
Go for DevOps: Learn how to use the Go language to automate servers, the cloud, Kubernetes, GitHub, Packer, and Terraform [Doak, John, Justice, David] on Amazon.com. *FREE* shipping on qualifying offers. Go for DevOps: Learn how to use the Go language to automate servers, the cloud, Kubernetes, GitHub, Packer, and Terraform

Acronyms are shortcuts, and we love using them, specially the catchy ones! Let's decipher some...

Learn about the modern tools for data orchestration, data storage, analytical engineering, batch processing, and data streaming.

A list of popular SSH commands for SSH connections, key generation & SSH agents that I'm using on a daily basis.

One way to achieve this is by employing uptime and downtime monitoring tools. Why Is Website Uptime Monitoring Important? An uptime monitoring solution can help you prevent or reduce these losses. Thus, you must employ a dependable tool that detects downtime or any interruptions related to your…

As more companies strive to deliver software faster it becomes clear what legacy processes are...

The DDoS arms race shows no signs of slowing down.

Cloudflare is not the only service that helps you boost your website's speed and secure it. Here are some alternatives.

Jenkins job The jenkins job is an individual task that could be useful for your CI CD...

Overview of Github Actions Overview of Github Actions - Part 1 Overview of Github Actions...

Overview of Github Actions Overview of Github Actions - Part 1 Overview of Github Actions...

This is my personal story of starting the SRE organization at Uber. If you want advice rather than reminiscence, take a look at Trunk and Branches Model and Productivity in the age of hypergrowth. After I left SocialCode in 2014, I spent a month interviewing at a handful of companies trying to figure out what to do next. I was torn between two different paths: (1) leading engineering at a very small startup, or (2) taking a much smaller role at a fast growing company, with the expectation that growth would create opportunity. After some consideration, I took the latter path and joined Uber.
While I was leading PKC’s security practice, we did probably 20-30 code security audits, almost of all of them for startups that were just around their Series A or B (that was usually when they had cash and realized that it’d be good to take a deeper look at their security, after the do-or-die focus on product market fit).

Opinion on popular cloud service providers from an ML engineer

What exactly is this amazing tool? Infrastructure as code (IaC) tools allow you to manage...

In this article we are going to share two main things: The evolution of our infrastructure over...

And how to avoid them getting in there? — A surprisingly simple technique to handle it.

Explains how to fix "bash: add-apt-repository: command" error on an Ubuntu or Debian Linux system using the apt/apt-get command.
Hidden AWS data transfer costs can lead to higher than expected cloud service bills. This post will help track hidden fees and show you how to control them.
Since the foundation of the first public cloud companies in the early 2000s, they have radically transformed the landscape of the internet…

General Command Line Tools Autojump Autojump is a tool that learns your most...
139 votes, 93 comments. 352K subscribers in the devops community.
— Elitsa Krumova (@Eli_Krumova)

We present a novel approach to infiltrate data to air-gapped systems without any additional hardware on-site.

Welcome to the Top 10 (new) Web Hacking Techniques of 2021, the latest iteration of our annual community-powered effort to identify the most significant web security research released in the last year

This LambdaTest Jenkins Tutorial will help you learn the fundamentals of Jenkins and everything...

Recently the company I work for migrated to new servers. During this migration we were all fairly confident that our new architecture would work and would be able to sustain considerable traffic. How much traffic is "considerable traffic"? In all honesty, none of our team and even our consultants, could
An extended look at SSH features that can serve a variety of purposes for different use cases.
Get started with Gitlab in practicable time.
An evolving how-to guide for securing a Linux server. - imthenachoman/How-To-Secure-A-Linux-Server
How the heck do we run a massively popular website and asset resource while being funded primarily by donations?

This article explores 5 SSH best practices you should observe to boost the security of your infrastructure.

The Apache web server is the most popular way to serve web content on the internet. The Apache provides a modular and scalable server that can satisfy the n…

While writing a comparison of Kubernetes and Koyeb, we tried to determine how much operating a Kubernetes cluster really costs. This section of our comparison took us hours to write and ended up being so long that we decided to write a dedicated post about it. Kubernetes is a proven technology, but the true cost is often underestimated: this post investigates the actual financial costs of using Kubernetes.
Putting your IT infrastructure into the cloud seems to be the "in" thing. It's been around for a while, of course. And, like most things rel...

Say hello to a more convenient way to deploy your app. With just a few clicks, you can deploy your app directly from your repository!

Apache Mesos abstracts resources away from machines, enabling fault-tolerant and elastic distributed systems to easily be built and run effectively.

Security is both very important and often under-emphasized. While many targeted techniques help, there are some basic clean code habits which every developer can and should be doing
Here is four strong monitoring tools i would like to present for you. htop - interactive process viewer You may know the standard tool for watching real time processes on your machine top. If not, run $ top to see it in action, and $ man top to read the manual. The
A collection of inspiring lists, manuals, cheatsheets, blogs, hacks, one-liners, cli/web tools and more. - bjpcjp/the-book-of-secret-knowledge

Consul is a service networking solution to automate network configurations, discover services, and enable secure connectivity across any cloud or runtime.

DevOps is a collection of best practices for the software development process to shorten the development life cycle. Here is a comprehensive list of DevOps and Security terms you need to know.

This post is intended to be a guide for those that want to deploy a full-stack MERN app. It will be v...

Zabbix is a mature and effortless enterprise-class open source monitoring solution for network monitoring and application monitoring of millions of metrics.
Jenkins – an open source automation server which enables developers around the world to reliably build, test, and deploy their software
Monitor and troubleshoot workflows in complex distributed systems

Easily build, package, release, update, and deploy your project in any language—on GitHub or any external system—without having to run code yourself.
An open-source monitoring system with a dimensional data model, flexible query language, efficient time series database and modern alerting approach.
A curated list of amazingly awesome open source sysadmin resources inspired by Awesome PHP. - kahun/awesome-sysadmin

Want to know the history behind Puppet's famous State of DevOps reports? Get the full scoop in this ultimate resource.

DevOps is really hot at the moment and most of my friends, colleagues, and senior developers I know are working hard to become a DevOps engineer and project themselves as DevOps champion in their organization.
MicroK8s is the simplest production-grade conformant K8s. Lightweight and focused. Single command install on Linux, Windows and macOS. Made for devOps, great for edge, appliances and IoT. Full high availability Kubernetes with autonomous clusters and distributed storage.
Vagrant is a tool for building complete development environments. With an easy-to-use workflow and focus on automation, Vagrant lowers development environment setup time, increases development/production parity, and makes the "it works on my machine" excuse a relic of the past.

Modern application infrastructure is being transformed by containers. The question is: How do you get started?

Get the best continuous integration and delivery (CI/CD), in our cloud or on your own infrastructure. Start for free and scale as you grow.

Learn about common industry terms and definitions related to cybersecurity and application delivery from the experts at F5.

Terraform is an infrastructure as code tool that enables you to safely and predictably provision and manage infrastructure in any cloud.
The Patterns of Scalable, Reliable, and Performant Large-Scale Systems - binhnguyennus/awesome-scalability

OpenSSH server best security practices - protect your server from brute force attack on a UNIX / Linux / *BSD / Mac OS X operating systems.

Learn how to build a simple load balancer server in Go. Table of Contents: What is a Load...

Vagrant isolates dependencies and their configuration within a single disposable and consistent development environment.

App Platform is a platform as a service (PaaS) offering that lets you publish code directly to DigitalOcean servers without worrying about the underlying infrastructure, runtimes, or dependencies.

DevOps is a software development and delivery process. It emphasizes communication, collaboration between product management, software development, and operations professionals. Following is a curated

Every ops team has some manual procedures that they haven’t gotten around to automating yet. Toil can never be totally eliminated. Very often, the biggest toil center for a team at a growing …

Here are some commands to help me with my work. And what are your useful commands that you use? Sea...

Kubernetes is powerful, but that does not mean it’s the right choice for every team and every app. It is made to solve a certain set of problems.

Learn about common industry terms and definitions related to cybersecurity and application delivery from the experts at F5.

Shell is the essential tool for every programmer. The more familiar you become with the available too...

If you're on a Unix system you probably have to constantly interact with the terminal, one way or ano...

Kernel-based Virtual Machine (KVM) is a free and open-source virtualization module in the Linux kernel that allows the kernel to function as a hypervisor. It was merged into the mainline Linux kernel in version 2.6.20, which was released on February 5, 2007. KVM requires a processor with hardware virtualization extensions, such as Intel VT or AMD-V. KVM has also been ported to other operating systems such as FreeBSD and illumos in the form of loadable kernel modules.
A consistent developer workflow to build, deploy, and release applications across any platform.

Travis CI is the most simple and flexible ci/cd tool available today. Find out how Travis CI can help with continuous integration and continuous delivery.

A concise masterclass on how to write infrastructure code
Lessons learned from successful MLOps implementation
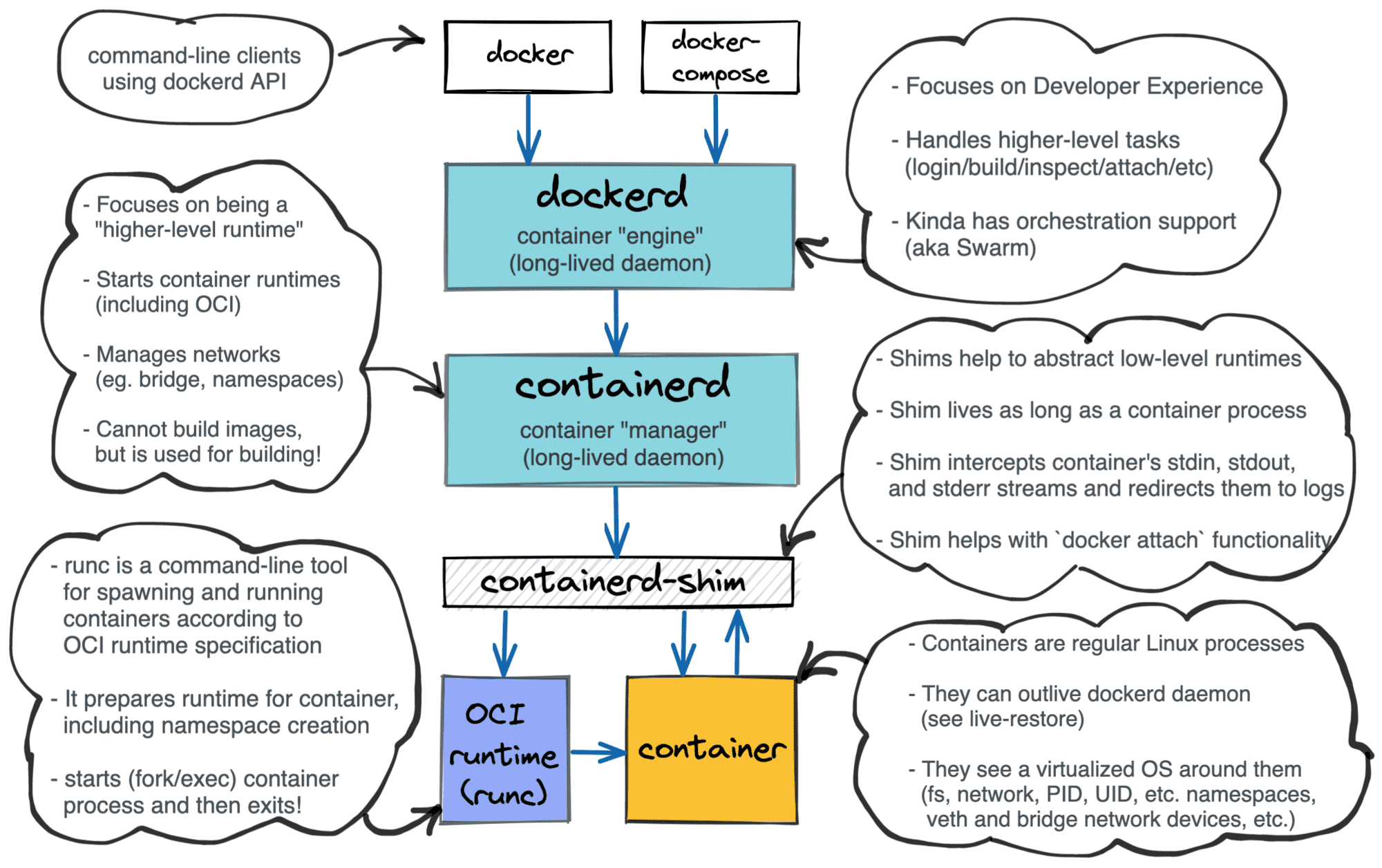
What is a Container? Container vs. VM? Docker vs. Kubernetes. How to organize the learning efficiently?

When considering tools to help optimize parts or all of your cloud incident remediation workflows and...
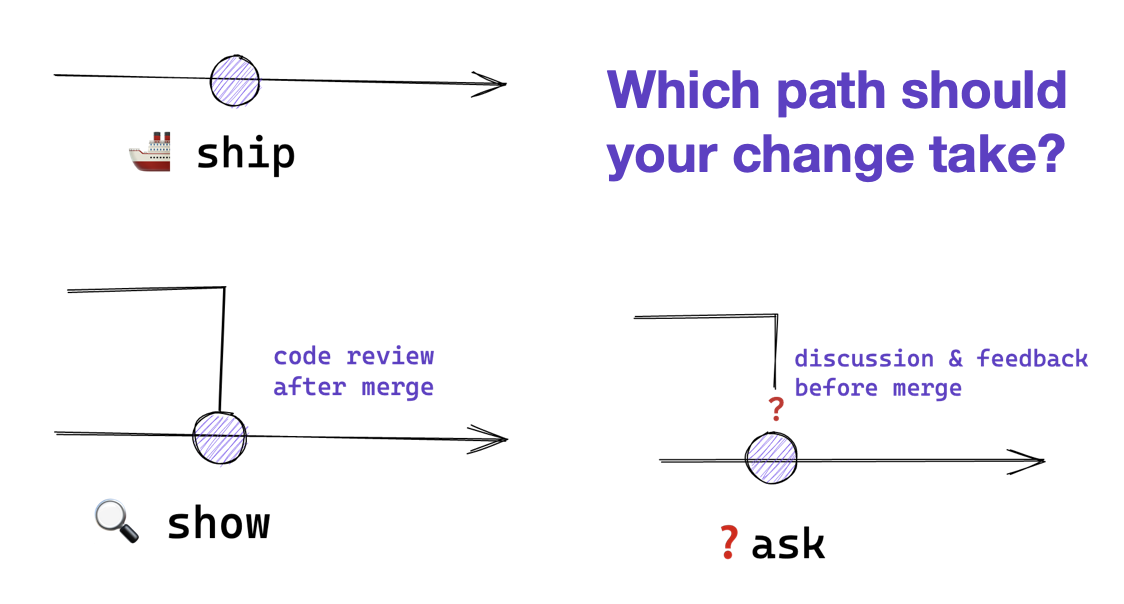
Ship/Show/Ask is a branching strategy that helps teams wait less and ship more, without losing out on feedback.

Organizing data using tags A tag is a label that you assign to an AWS resource. Each tag...

Tired of Big Tech monopolies, a community of hobbyists is taking their digital lives off the cloud and onto DIY hardware that they control.

Ansible What is Ansible? Ansible is an open-source IT Configuration...

You can build a functional CDN on an 8-year-old laptop while you're sitting at a coffee shop. Here's what a CDN you put together in five hours might look like.

Content by github.com/ripienaar/free-for-dev Contributors:...

An exhaustive list of 30 interesting server monitoring tools and services for you to explore!

“No, we don’t use Kubernetes”. That always gets raised eyebrows... so we decided to write about our reasoning behind this cloud architecture decision.

1. Kali Linux Kali Linux is the most used Ethical Hacking distro available, it is provided with...
Terraform enables you to safely and predictably create, change, and improve infrastructure. It is a source-available tool that codifies APIs into declarative configuration files that can be shared ...

This AWS DevOps Engineer Certification Bundle contains 11 Courses on AWS Database, Cloud Automation, Lambda, & More! Become a DevOps engineer.
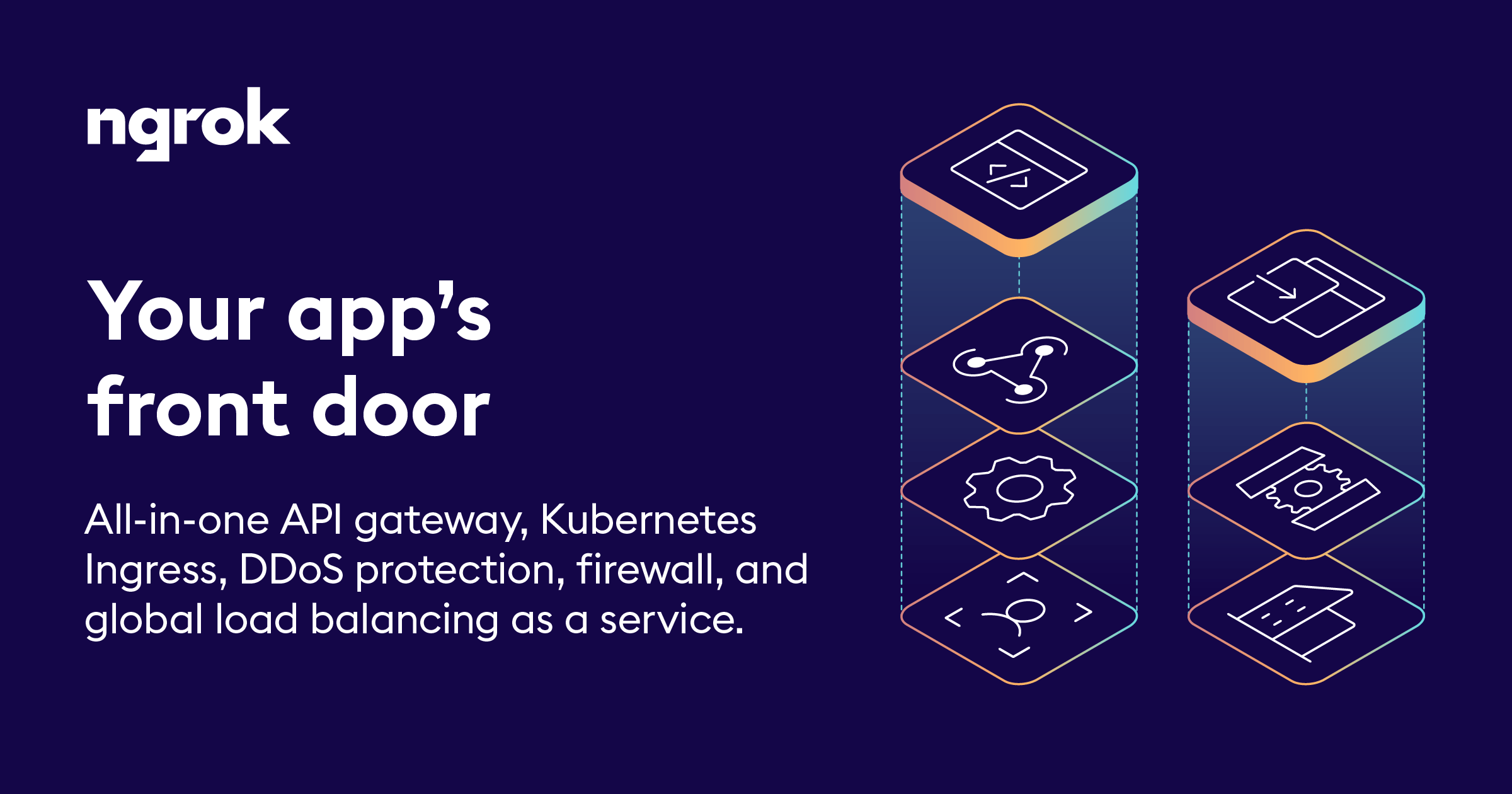
ngrok is a secure ingress platform that enables developers to add global server load balancing, reverse proxy, firewall, API gateway and Kubernetes Ingress to applications and APIs.

Voice123 is the first (and arguably foremost) open marketplace for voice actors. Today, Voice123 ha...

What is Site Reliability Engineering (SRE)? The site reliability engineering (SRE) conce...
At Channable we use Nix to build and deploy our services and to manage our development environments. This was not always the case: in the past we used a combination of ecosystem-specific tools and custom scripts to glue them together. Consolidating everything with Nix has helped us standardize development and deployment workflows, eliminate “works on my machine”-problems, and avoid unnecessary rebuilds. In this post we want to share what problems we encountered before adopting Nix, how Nix solves those, and how we gradually introduced Nix into our workflows.

As grandiose as the title of this article might sound, I should clarify we’re talking about a low-stress, one-person company that I run from my flat here in Germany.
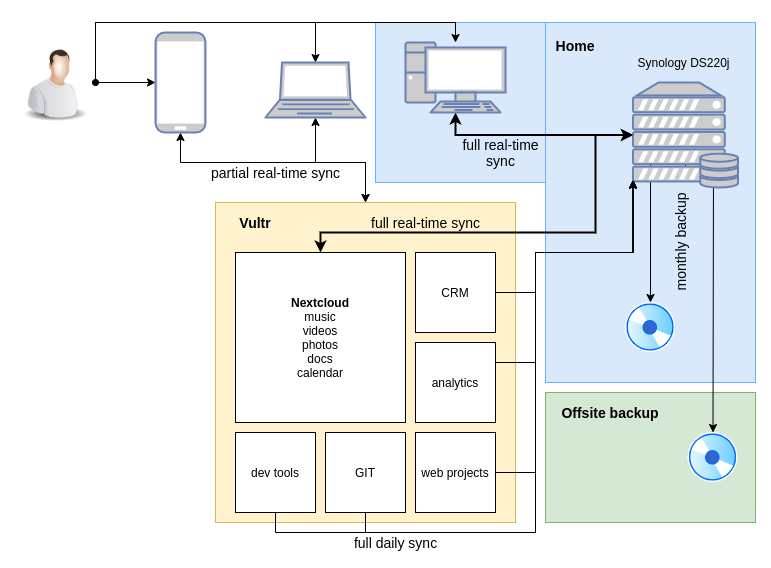
It’s all fun and games until someone loses an eye. Likewise, it’s all fun and games until someone loses access to their private and/or business data because they trusted it to someone else.

This article demonstrates the deployment of a basic Streamlit app (that simulates the Central Limit Theorem) to Heroku.

Although phishing tests can be helpful to protect users, using questionable tactics has the potential for harming relationships between a company and its employees. The authors suggest that managers avoid this damage by employing phishing tests with three criteria: Test teams, not individuals; don’t embarrass anyone; and gamify and reward.
A few weeks ago an ordinary security assessment turned into an incident response whirlwind. It was definitely a first for me, and I was kindly granted permission to outline the events in this blog post. This investigation started scary but turned out be quite fun, and I hope reading it will be informative to you too. I'll be back to posting about my hardware research soon. How it started What hell is this? The NFS Server 2nd malicious binary Further forensics Eureka Moment The GOlang thingy How the kernel got patched? and why not the golang app? What we have so far Q&A How it started Twice a year I am hired to do security assessments for a specific client. We have been working together for several years, and I had a pretty good understanding of their network and what to look for. This time my POC, Klaus, asked me to focus on privacy issues and GDPR compliance. However, he asked me to first look at their cluster of reverse gateways / load balancers: I had some prior knowledge of these gateways, but decided to start by creating my own test environment first. The gateways run a custom Linux stack: basically a monolithic compiled kernel (without any modules), and a static GOlang application on top. The 100+ machines have no internal storage, but rather boot from an external USB media that has the kernel and the application. The GOlang app serves in two capacities: an init replacement and the reverse gateway software. During initialization it mounts /proc, /sys, devfs and so on, then mounts an NFS share hardcoded in the app. The NFS share contains the app's configuration, TLS certificates, blacklist data and a few more. It starts listening on 443, filters incoming communication and passes valid requests on different services in the production segment. I set up a self contained test environment, and spent a day in black box examination. Having found nothing much I suggested we move on to looking at the production network, but Klaus insisted I continue with the gateways. Specifically he wanted to know if I could develop a methodology for testing if an attacker has gained access to the gateways and is trying to access PII (Personally Identifiable Information) from within the decrypted HTTP stream. I couldn't SSH into the host (no SSH), so I figured we will have to add some kind of instrumentation to the GO app. Klaus still insisted I start by looking at the traffic before (red) and after the GW (green), and gave me access to a mirrored port on both sides so I could capture traffic to a standalone laptop he prepared for me and I could access through an LTE modem but was not allowed to upload data from: The problem I faced now was how to find out what HTTPS traffic corresponded to requests with embedded PII. One possible avenue was to try and correlate the encrypted traffic with the decrypted HTTP traffic. This proved impossible using timing alone. However, unspecting the decoded traffic I noticed the GW app adds an 'X-Orig-Connection' with the four-tuple of the TLS connection! Yay! I wrote a small python program to scan the port 80 traffic capture and create a mapping from each four-tuple TLS connection to a boolean - True for connection with PII and False for all others: 10.4.254.254,443,[Redacted],43404,376106847.319,False 10.4.254.254,443,[Redacted],52064,376106856.146,False 10.4.254.254,443,[Redacted],40946,376106856.295,False 10.4.254.254,443,[Redacted],48366,376106856.593,False 10.4.254.254,443,[Redacted],48362,376106856.623,True 10.4.254.254,443,[Redacted],45872,376106856.645,False 10.4.254.254,443,[Redacted],40124,376106856.675,False ... With this in mind I could now extract the data from the PCAPs and do some correlations. After a few long hours getting scapy to actually parse timestamps consistently enough for comparisons, I had a list of connection timing information correlated with PII. A few more fun hours with Excel and I got histogram graphs of time vs count of packets. Everything looked normal for the HTTP traffic, although I expected more of a normal distribution than the power-low type thingy I got. Port 443 initially looked the same, and I got the normal distribution I expected. But when filtering for PII something was seriously wrong. The distribution was skewed and shifted to longer time frames. And there was nothing similar on the port 80 end. My only explanation was that something was wrong with my testing setup (the blue bars) vs. the real live setup (the orange bars). I wrote on our slack channel 'I think my setup is sh*t, can anyone resend me the config files?', but this was already very late at night, and no one responded. Having a slight OCD I couldn’t let this go. To my rescue came another security? feature of the GWs: Thet restarted daily, staggered one by one, with about 10 minutes between hosts. This means that every ten minutes or so one of them would reboot, and thus reload it’s configuration files over NFS. And since I could see the NFS traffic through the port mirror I had access to, I recokoned I could get the production configuration files from the NFS capture (bottom dotted blue line in the diagram before). So to cut a long story short I found the NFS read reply packet, and got the data I need. But … why the hack is eof 77685??? Come on people, its 3:34AM! What's more, the actual data was 77685 bytes, exactly 8192 bytes more then the ‘Read length’. The entropy for that data was pretty uniform, suggesting it was encrypted. The file I had was definitely not encrypted. Histogram of extra 8192 bytes: When I mounted the NFS export myself I got a normal EOF value of 1! What hell is this? Comparing the capture from my testing machine with the one from the port mirror I saw something else weird: For other NFS open requests (on all of my test system captures and for other files in the production system) we get: Spot the difference? The open id: string became open-id:. Was I dealing with some corrupt packet? But the exact same problem reappeared the next time blacklist.db was send over the wire by another GW host. Time to look at the kernel source code: The “open id” string is hardcoded. What's up? After a good night sleep and no beer this time I repeated the experiment and convincing myself I was not hullucinating I decided to compare the source code of the exact kernel version with the kernel binary I got. What I expected to see was this (from nfs4xdr.c): static inline void encode_openhdr(struct xdr_stream *xdr, const struct nfs_openargs *arg) { __be32 *p; /* * opcode 4, seqid 4, share_access 4, share_deny 4, clientid 8, ownerlen 4, * owner 4 = 32 */ encode_nfs4_seqid(xdr, arg->seqid); encode_share_access(xdr, arg->share_access); p = reserve_space(xdr, 36); p = xdr_encode_hyper(p, arg->clientid); *p++ = cpu_to_be32(24); p = xdr_encode_opaque_fixed(p, "open id:", 8); *p++ = cpu_to_be32(arg->server->s_dev); *p++ = cpu_to_be32(arg->id.uniquifier); xdr_encode_hyper(p, arg->id.create_time); } Running binwalk -e -M bzImage I got the internal ELF image, and opened it in IDA. Of course I didn’t have any symbols, but I got nfs4_xdr_enc_open() from /proc/kallsyms, and from there to encode_open() which led me to encode_openhdr(). With some help from hex-rays I got code that looked very similiar, but with one key difference: static inline void encode_openhdr(struct xdr_stream *xdr, const struct nfs_openargs *arg) { ... p = xdr_encode_opaque_fixed(p, unknown_func("open id:", arg), 8); ... } The function unknown_func was pretty long and complicated but eventually sometimes decided to replace the space between 'open' and 'id' with a hyphen. Does the NFS server care? Apparently this string it is some opaque client identifier that is ignored by the NFS server, so no one would see the difference. That is unless they were trying to extract something from an NFS stream, and obviously this was not a likely scenario. OK, back to the weird 'eof' thingy from the NFS server. The NFS Server The server was running the 'NFS-ganesha-3.3' package. This is a very modular user-space NFS server that is implemented as a series of loadable modules called FSALs. For example support for files on the regular filesystem is implemented through a module called libfsalvfs.so. Having verified all the files on disk had the same SHA1 as the distro package, I decided to dump the process memory. I didn't have any tools on the host, so I used GDB which helpfully was already there. Unexpectadly GDB was suddenly killed, the file I specified as output got erased, and the nfs server process restarted. I took the dump again but there was nothing special there! I was pretty suspicious at this time, and wanted to recover the original dump file from the first dump. Fortunately for me I was dumping the file to the laptop, again over NFS. The file had been deleted, but I managed to recover it from the disk on that server. 2nd malicious binary The memory dump was truncated, but had a corrupt version of NFS-ganesha inside. There were two libfsalvfs.so libraries loaded: the original one and an injected SO file with the same name. The injected file was clearly malicious. The main binary was patched in a few places, and the function table into libfsalvfs.so as replaced with the alternate libfsalvfs.so. The alternate file was compiled from NFS-ganesha sources, but modified to include new and improved (wink wink) functionality. The most interesting of the new functionality were two separate implementations of covert channels. The first one we encountered already: When an open request comes in with 'open-id' instead of 'open id', the file handle is marked. This change is opaque to the NFS server, so unpatched servers just ignore it and nothing much happens. For infiltrated NFS server, when the file handle opened this way is read, the NFS server appends the last block with a payload coming from the malwar...

News & blog about Learn Enough (including the Ruby on Rails Tutorial)

Detectify analyzed 50,000 unique Nginx configuration files on GitHub and reported some common misconfigurations.

News & blog about Learn Enough (including the Ruby on Rails Tutorial)

Custom domains for websites, web apps, and email

Performance Action Pack consists of tools and techniques to efficiently audit and optimize your Ruby on Rails application.

Read more on the Doximity Technology Blog about how our engineers and data scientists are building the largest online network for clinicians.
A methodology for building modern, scalable, maintainable software-as-a-service apps.
Discover the free cloud features that come with the Google Cloud trial offer and more information on how to upgrade your account.

An independent, reader-supported publication focusing on Linux Command Line, Server, Self-hosting, DevOps and Cloud Learning
33 votes, 56 comments. Heroku is easy to use and has a good marketplace. They make it really easy to deploy and to purchase additional resources. I…

Did you know there's an easier way to mount your secondary hard drive on Linux? The process involves a few simple edits to the fstab file on your system.

A tutorial on how to build a GitHub App that predicts and applies issue labels using Tensorflow and public datasets.

Source code: Lib/shutil.py The shutil module offers a number of high-level operations on files and collections of files. In particular, functions are provided which support file copying and removal...
77 votes, 16 comments. This course has been running successfully now every month since February 2020 - more detail at…

Power-up Your Workflow with Cloud instance!
Cloud Functions are Google’s offering for serverless architecture (similar to AWS lambdas). What is serverless? Before we look into how to use Cloud Functions, we should understand some things about it. Code needs servers to run, so serverless doesn’t mean there are no servers, it means that we don’t need to manage those servers ourselves. In a usual server based architecture, we might create a service and deploy it to a machine. This service will be running in the machine all the time waiting for requests. This has the disadvantage that even if there are no requests, the machine would need to be up, and incurring cost. On the other hand, if we use Cloud Functions, we write a service and register it with Google. Google will then listen to the endpoint this service cares about and will only start it when there are requests. If it detects that there haven’t been requests for some time, it will stop the service again.

Get started with Azure App Service by deploying your first Python app to Azure App Service.

The newest layer of abstraction by Gruntwork that’ll make your life easier

Preparing your Infrastructure as Code solution? Ansible and Terraform are two of the most popular choices. But what's the difference?

This article explains why Docker is now deprecated in Kubernetes.
Free Introduction to Bash Scripting eBook.
After leaving Google, many engineers miss the developer tools. Here's one ex-Googler's guide to navigating the dev tools landscape outside of Google, finding the ones that fill the gaps you're feeling, and introducing these to your new team.
Build better websites with real-time traffic, performance and error monitoring. Start your free 14 day trial.

This post was originally published on November 12, 2020, but the content has been updated according to the recent Ansible changes. In our previous blog post , we looked at what configuration management tools bring to the table. And in this post, we will take a closer look at Ansible, our configuration management tool of choice. So if you want to learn what Ansible is, what it does, and how it works, this is the post for you.
Writing a container in a few lines of Go code, as seen at DockerCon 2017 and on O'Reilly Safari - rewanthtammana/containers-from-scratch
Even though I’ve developed software for a number of years now, there’s one question that has always been in the back of my mind and I haven’t had the time or patience to really answer, until now: What is a binary executable anyways?
Expose your local web server to the internet with a public URL

Google Cloud buildpacks make it much easier and faster to build applications on top of containers.

In this post I'll outline several ways to build containers without the need for Docker itself including buildkit, kaniko, GitHub Actions, GitLab and Jenkins

SLOs are a lot easier with a service mesh in han. In this tutorial, you’ll learn how to easily create service health SLOs on Kubernetes with Prometheus, an open source time-series database, and Linkerd, an open source ultralight service mesh. You’ll see how using a service mesh can solve one of the...
Overview The Docker driver allows you to install Kubernetes into an existing Docker install. On Linux, this does not require virtualization to be enabled. Requirements Install Docker 18.09 or higher (20.10 or higher is recommended) amd64 or arm64 system. If using WSL complete these steps first Usage Start a cluster using the docker driver: minikube start --driver=docker To make docker the default driver: minikube config set driver docker Requirements Docker 20.10 or higher, see https://rootlesscontaine.rs/getting-started/docker/ Cgroup v2 delegation, see https://rootlesscontaine.rs/getting-started/common/cgroup2/ Kernel 5.11 or later (5.13 or later is recommended when SELinux is enabled), see https://rootlesscontaine.rs/how-it-works/overlayfs/ Usage Start a cluster using the rootless docker driver:

Find bugs, run security scans in CI, and enforce security standards across your organization.

GitHub CLI brings GitHub to your terminal. It reduces context switching, helps you focus, and enables you to more easily script and create your own workflows. Earlier this year, we…
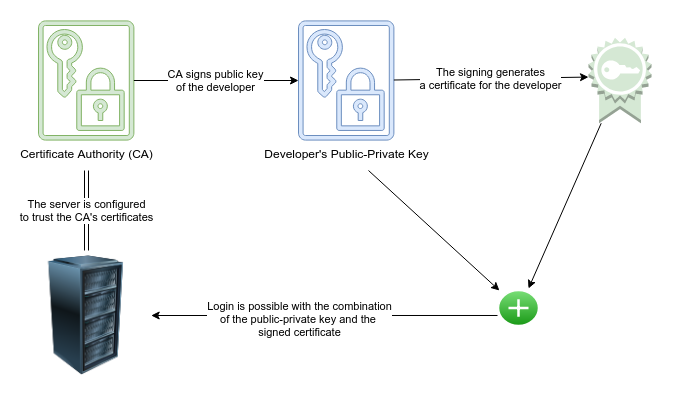
This article was on the hacker news frontpage. You can find the related discussion here. Every developer needs access to some servers for example to check the application logs. Usually, this is done using public-private key encryption where each developer generates their own public-private key pair. The public keys of each developer are added to the authorized_keys file on each server they should have access to. Painful manual changes So far so good.
Example code and files from "Kubernetes: Up and Running" - kubernetes-up-and-running/examples

Explore what a container is, how its created, how it compares to virtual machines, and its use cases. Learn how Sumo Logic's integration for Docker containers enables IT teams to analyze, troubleshoot and perform root cause analysis of issues surfacing from distributed container-based applications and from Docker containers themselves.

Learn how to set up a real-world, production-ready Kubernetes cluster using Amazon Elastic Kubernetes Service (Amazon EKS) and Terraform.

Have you ever wondered how companies like Facebook are able to serve applications to Billions of...

Encyclopedia of databases systems from Carnegie Mellon University. Curated by @andy_pavlo

December 10, 2020 – Post updated for the extension of the T4g free-trial until March 31, 2021. During the free-trial period, customers who run a t4g.micro instance will automatically get 750 free hours per month deducted from their bill during each month. T4g free-trial will be available in addition to the existing AWS Free-Tier on […]

A look at one of the most popular build systems for C and C++.
The ultimate guide to dynos on Heroku. If you’ve ever asked "how many dynos do I need?" or "which dyno type is right for my app?", this is the guide for you.

This week I explored Terraform as part of my exploration of development and operations topics. Terraform is a tool for automating the…

Deliver Infrastructure and Software running on it Rapidly and Reliably at Scale

Network-Mapper (NMap), is the most famous scanning tool used by penetration testers. In this article, we will look at some core features…

Worried about the security of your Linux server? Learn some easy to implement tips on securing SSH and make your Linux server more secure.

Learn about useful networking commands that are pre-installed on your computer and will help you know everything about a website.

Google says Tsunami is an extensible network scanner for detecting high-severity vulnerabilities with as little false-positives as possible.

Previously, I wrote about my favorite Mac apps. But I spend half of my time in the terminal, and I ha...

Even though the DevOps methodology has been with us for quite some time now, it’s still the center of heated discussions. Companies want it but are unsure of how to approach it. DevOps is everywhere. And while it’s an interesting trend, it

The tech stack of Listen Notes, the best podcast search engine and database.
Overview of deploying a model with the Chef — A Configuration Management Tool
Investigation of the practice of port scanning site visitors for fingerprinting and tracking.
Start learning with step-by-step, hands-on, command-line tutorials, videos, and hosted terminal sessions. Actionable examples help you learn to provision, secure, connect, or run any application on any infrastructure.

Search and browse cloud infrastructure services such as PaaS, IaaS, log management, exception monitoring, realtime backend APIs, and more. Find the right tools and services to build your next app.

Install Terraform on Mac, Linux, or Windows by downloading the binary or using a package manager (Homebrew or Chocolatey). Then create a Docker container locally by following a quick-start tutorial to check that Terraform installed correctly.

This new Python package accelerates notebook-based machine learning experimentation
Deploy, scale and manage your machine learning services with Kubernetes and Terraform on GCP.
A project template and directory structure for Python data science projects.
Research domain ownership with Whois Lookup: Get ownership info, IP address history, rank, traffic, SEO & more. Find available domains & domains for sale.

Helping millions of developers easily build, test, manage, and scale applications of any size — faster than ever before.
A hands-on DevOps course covering the culture, methods and repeated practices of modern software development involving Packer, Vagrant, VirtualBox, Ansible, Kubernetes, K3s, MetalLB, Traefik, Docke...

Jenkins – an open source automation server which enables developers around the world to reliably build, test, and deploy their software
Ansible is an open source, command-line IT automation software application written in Python. It can configure systems, deploy software, and orchestrate advanced workflows to support application deplo
Ansible for DevOps examples.
Having some issues to get my vagrant up, Got the box, run vagrant init and after vagrant up command I get this message. Bringing machine 'default' up with 'virtualbox' provider... ==> defa...
Load Balancers plays a key role in Web Architecture. In this post we are going to develop a simple load balancer with power of Go
Measure your site reliability metrics, set the right targets, and go through the work to measure the metrics accurately. Then, you

Build and manage real-life ML, AI, and data science projects with Metaflow.

Domain names provide the internet much more user-friendly way of referencing servers, but have you ever wondered how it works under the covers?

The tech stack of Listen Notes, the best podcast search engine and database.

Learn the secrets of Rails deployment and everything it takes to successfully run your application in the wild.
In this article, you will explore how you can leverage Kubernetes, Tensorflow and Kubeflow to scale your models without having to worry about scaling the infrastructure.

Git, GitHub, Visual Studio Code, Docker, and npm are the most popular tools in the category "DevOps". "Distributed version control system" is the primary reason developers pick Git over its competitors, while "Open source friendly" is the reason why GitHub was chosen.

Developing and releasing software can be a complicated process, especially as applications, teams, and deployment infrastructure grow in complexity themselve…
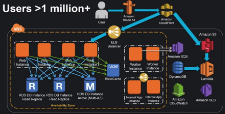
How do you scale a system from one user to more than 11 million users? Joel Williams, Amazon Web Services Solutions Architect, gives an excellent talk on just that subject: AWS re:Invent 2015 Scaling Up to Your First 10 Million Users. If you are an advanced AWS user this

Certificates and public key infrastructure (PKI) are hard. No shit, right? I know a lot of smart people who''ve avoided this particular rabbit hole. Eventually, I was forced to learn this stuff because of what it enables: PKI lets you define a system cryptographically. It''s universal and vendor-neutral yet poorly documented. This is the missing manual.

Realize the speed, agility and performance of a scalable, composable web architecture with Netlify. Explore the composable web platform now!

The OpenStack Foundation today released the 18th version of its namesake open-source cloud infrastructure software. The project has had its ups and downs,

Sometimes people want to get a certificate for the hostname “localhost”, either for use in local development, or for distribution with a native application that needs to communicate with a web application. Let’s Encrypt can’t provide certificates for “localhost” because nobody uniquely owns it, and it’s not rooted in a top level domain like “.com” or “.net”. It’s possible to set up your own domain name that happens to resolve to 127.
Linux load averages explained, including why they include the uninterruptible I/O sleep state.
I’m going to describe a way to put together a world-class continuous deployment infrastructure for your side-project without spending any money. With continuous deployment every code commit is tested against …

The SSH port is 22. This is the story of how it got that port number. And practical configuration instructions.

Answer (1 of 7): Lots. Definitions of the term "data centre" tend to vary. Some would label a small machine room with 2 or 3 racks a data centre, but that is not really a large facility by any stretch of the imagination. Most such installations are never going to hit the usual problems which dat...

Achieving very low latencies takes special engineering, but if you are a SaaS company latencies of a few hundred milliseconds are possible for complex business logic using standard technologies like load balancers, queues, JVMs, and rest APIs. Itai Frenkel, a software engineer at Forter, which provides a Fraud Prevention Decision